
Home • Регистрация • FAQ • Поиск • Вход |
| Сообщения без ответов | Активные темы | Текущее время: 23 апр 2021, 04:13
|
Anyconnect доступ в несколько сетейМодератор: Fedia
Страница 1 из 1
| [ Сообщений: 3 ] |
| Версия для печати | Пред. тема | След. тема |
| Автор | Сообщение |
|---|
Зарегистрирован: 20 май 2012, 20:30
Сообщения: 16
| Есть Cisco ASA 5505 на ней поднят Anyconnect так чтобы клиент видел внутренние ресурсы и выходил через неё в интернет. Клиент подключается к ней и видит сеть 10.1.0.0/24 и спокойно ходит в интернет, но не может подключится к хостам в 10.1.3.0/24 и не имеет доступа к самой ASA. Как сделать так чтобы клиент подключившейся с помощью anyconnect видел все сети и мог подключится к ASA по ssh? Вот конфигурация c ASA: home-gw-1(config)# sh run
: Saved
:
ASA Version 8.4(4)
!
hostname home-gw-1
domain-name home.local
enable password 2KFQnbNIdI.2KYOU encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
name 10.1.0.1 gw
!
interface Ethernet0/0
description isp
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
description home-sw-core
switchport trunk allowed vlan 2,10,13
switchport mode trunk
!
interface Vlan1
no nameif
no security-level
no ip address
!
interface Vlan2
description ISP-ONLIME
nameif outside
security-level 0
ip address dhcp setroute
!
interface Vlan10
description LAN
nameif inside
security-level 100
ip address gw 255.255.255.0
!
interface Vlan13
description management
nameif mgt
security-level 100
ip address 10.1.3.1 255.255.255.0
!
boot system disk0:/asa844-k8.bin
boot config disk0:/startup-config
ftp mode passive
clock timezone MSK 4
dns domain-lookup inside
dns server-group DefaultDNS
name-server 77.37.255.30
name-server 77.37.251.33
domain-name home.local
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network C1
host 10.1.0.99
object network OBJ-ANYCONNECT-POOL
subnet 10.1.1.0 255.255.255.0
object network OBJ-USERS
subnet 10.1.0.0 255.255.255.0
object network OBJ-MGT
subnet 10.1.3.0 255.255.255.0
access-list INSIDE-ACL-IN extended permit ip object OBJ-USERS any
access-list INSIDE-ACL-OUT extended permit ip any object OBJ-USERS
access-list MGT-ACL-IN extended permit ip object OBJ-MGT any
access-list MGT-ACL-OUT extended permit ip any object OBJ-MGT
access-list OUTSIDE-ACL-IN extended permit ip any any
access-list OUTSIDE-ACL-OUT extended permit ip any any
pager lines 24
logging enable
logging asdm informational
mtu outside 1500
mtu inside 1500
mtu mgt 1500
ip local pool vpn-pool 10.1.1.10-10.1.1.35 mask 255.255.255.0
no failover
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-649.bin
no asdm history enable
arp timeout 14400
nat (mgt,outside) source static OBJ-MGT OBJ-MGT destination static OBJ-ANYCONNECT-POOL OBJ-ANYCONNECT-POOL no-proxy-arp
nat (inside,outside) source static OBJ-USERS OBJ-USERS destination static OBJ-ANYCONNECT-POOL OBJ-ANYCONNECT-POOL no-proxy-arp
!
object network C1
nat (inside,outside) static interface service tcp 22000 22000
object network OBJ-ANYCONNECT-POOL
nat (outside,outside) dynamic interface
object network OBJ-USERS
nat (inside,outside) dynamic interface
object network OBJ-MGT
nat (mgt,outside) dynamic interface
access-group OUTSIDE-ACL-IN in interface outside
access-group OUTSIDE-ACL-OUT out interface outside
access-group INSIDE-ACL-IN in interface inside
access-group INSIDE-ACL-OUT out interface inside
access-group MGT-ACL-IN in interface mgt
access-group MGT-ACL-OUT out interface mgt
route inside 10.1.4.0 255.255.255.0 10.1.0.2 1
route inside 10.10.0.0 255.255.0.0 10.1.0.70 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
http 10.1.0.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
telnet timeout 5
ssh 10.1.1.0 255.255.255.0 outside
ssh 10.1.0.0 255.255.255.0 inside
ssh 10.1.3.0 255.255.255.0 mgt
ssh timeout 60
ssh version 2
ssh key-exchange group dh-group1-sha1
console timeout 0
management-access inside
dhcpd lease 86400
dhcpd auto_config outside
!
dhcpd address 10.1.0.100-10.1.0.200 inside
dhcpd enable inside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ntp server 62.117.76.141
ntp server 62.117.76.142
ntp server 195.2.64.5
webvpn
enable outside
anyconnect-essentials
anyconnect image disk0:/anyconnect-win-2.3.2016-k9.pkg 1
anyconnect enable
tunnel-group-list enable
group-policy GroupPolicy_anyconnect internal
group-policy GroupPolicy_anyconnect attributes
wins-server none
dns-server value 8.8.8.8
vpn-tunnel-protocol ssl-client
default-domain value home.local
username XXXX password XXXXXXXXXXXXXX encrypted privilege 15
tunnel-group anyconnect type remote-access
tunnel-group anyconnect general-attributes
address-pool vpn-pool
default-group-policy GroupPolicy_anyconnect
nat-assigned-to-public-ip inside
tunnel-group anyconnect webvpn-attributes
group-alias anyconnect enable
!
class-map inspection_default
!
!
policy-map global_policy
class inspection_default
inspect icmp
inspect ctiqbe
inspect dcerpc
inspect dns
inspect esmtp
inspect ftp
inspect h323 h225
inspect h323 ras
inspect http
inspect icmp error
inspect ils
inspect ip-options
inspect mgcp
inspect netbios
inspect pptp
inspect rsh
inspect rtsp
inspect sip
inspect skinny
inspect snmp
inspect sqlnet
inspect sunrpc
inspect waas
inspect xdmcp
inspect tftp
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
Cryptochecksum:0df26896e70c035e13c19bec3b3180e5
: end Топология: packet-tracer: home-gw-1(config)# packet-tracer input outside tcp 10.1.1.11 ssh 10.1.0.2 ssh
Phase: 1
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (inside,outside) source static OBJ-USERS OBJ-USERS destination static OBJ-ANYCONNECT-POOL OBJ-ANYCONNECT-POOL no-proxy-arp
Additional Information:
NAT divert to egress interface inside
Untranslate 10.1.0.2/22 to 10.1.0.2/22
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group OUTSIDE-ACL-IN in interface outside
access-list OUTSIDE-ACL-IN extended permit ip any any
Additional Information:
Phase: 3
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 4
Type: CP-PUNT
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 5
Type: WEBVPN-SVC
Subtype: in
Result: DROP
Config:
Additional Information:
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: inside
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
home-gw-1(config)# packet-tracer input outside tcp 10.1.1.11 ssh 10.1.3.2 ssh
Phase: 1
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (mgt,outside) source static OBJ-MGT OBJ-MGT destination static OBJ-ANYCONNECT-POOL OBJ-ANYCONNECT-POOL no-proxy-arp
Additional Information:
NAT divert to egress interface mgt
Untranslate 10.1.3.2/22 to 10.1.3.2/22
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group OUTSIDE-ACL-IN in interface outside
access-list OUTSIDE-ACL-IN extended permit ip any any
Additional Information:
Phase: 3
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 4
Type: CP-PUNT
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 5
Type: WEBVPN-SVC
Subtype: in
Result: DROP
Config:
Additional Information:
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: mgt
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
ping с home-sw-core: home-sw-core#ping 10.1.3.1 source vlan 13
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.3.1, timeout is 2 seconds:
Packet sent with a source address of 10.1.3.2
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/6 ms
home-sw-core#ping 10.1.0.1 source vlan 10
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.0.1, timeout is 2 seconds:
Packet sent with a source address of 10.1.0.2
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/10 ms
| | 06 май 2014, 15:30 |
Зарегистрирован: 10 окт 2012, 09:51
Сообщения: 2678
| а вы уверены что в инет ходит через вас?
Я что-то не увидел у вас в конфиге, какие маршруты вы передаете клиенту. Вот не помню, передается по-умолчанию default или нет.
| | 06 май 2014, 17:45 | 2 crash
Маршрут передаётся. В интернет клиент ходит через асу.
| | 06 май 2014, 21:46 |
Страница 1 из 1
| [ Сообщений: 3 ] |
Кто сейчас на конференции | Сейчас этот форум просматривают: Google [Bot] и гости: 55 |
Вы не можете начинать темы
Вы не можете отвечать на сообщения
Вы не можете редактировать свои сообщения
Вы не можете удалять свои сообщения
Вы не можете добавлять вложения
|
Создано на основе phpBB® Forum Software © phpBB Group
Designed by ST Software for PTF.
Русская поддержка phpBB |
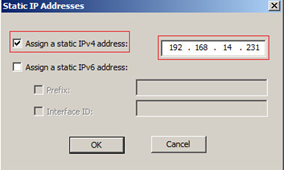
For example, 192.168.1.10 - 192.168.1.253, leaving 192.168.1.1 to 192.168.1.9 in my static IP addresses under Dial-up Tab in the Windows AD??? What I want to happen is the Cisco ASA will still assign random IP addresses to AnyConnect VPN users but for certain LDAP users, they should have specific.
Overview
When using a Cisco ASA with the AnyConnect VPN Client software in some instances it is useful to assign the same static IP address to a client whenever they connect to the VPN. Within Active Directory you can configure per user a static IP address and use this IP address whenever the user connects to the VPN. The RADIUS Server (in this instance Cisco ISE 2.0) can be configured to query the attribute in AD which is the” msRADIUSFramedIPAddress” value and assign to the client whenever they connect.
This post only describes configuring a static IP address on a Cisco AnyConnect Remote Access VPN. Refer to the following posts for more detail instructions on how to configure ASA Remote Access VPN and integrated with Cisco ISE for authentication:
ASA AnyConnect SSL-VPN
ASA AnyConnect IKEv2/IPSec VPN
Software/Hardware Used:
Hi, So I have Anyconnect VPN configured on my ASA and users are being authenticated via ACS. My requirement is to provide static IP for all users. I have configured pool on ASA and after that I configured Framed IP on ACS. When connecting for first time, the user gets the same IP but after disconnection, the user gets a different pool IP. Over a static route: use the IP address of the MX/Z on the subnet shared with the next hop Over VPN: use the IP address of the MX/Z on the highest-numbered VLAN in VPN Create and enter a RADIUS Shared Secret (make note of this secret, you will need to add this to the dashboard). To exclude a range of IP addresses from the static address pool, type the starting IP address of the range that you want to exclude in the From box, type the ending IP address of the range that you want to exclude in the To box, and then select Add. Select OK, select OK, and then select Continue. Select the Protocols tab, select TCP/IP Protocol Properties.
Mac best latex editor. Windows 7 SP1 (Client)
Windows 2008 R2 (Active Directory Domain Controller)
Cisco ISE 2.0 (RADIUS Server)
Cisco ASAv v9.6(1)
Cisco AnyConnect Client 4.2.01022
Cisco ASA Configuration
- Modify the existing IP Address Pool to decrease the number of IP addresses, leaving space at the end of the range (or beginning) to be used for statically assigned IP addresses.
AD Account Modification
- Select a test account within AD
- Modify the properties of the test account; select the “Dial-in” tab
- Tick the “Assign Static IP Address” box
- Click the “Static IP Address” button
- Tick “Assign a static IPv4 address” box and enter and IP address from within the IP address range defined on the Cisco ASA appliances
- Click “OK” to complete the configuration
Cisco ISE Configuration
Add AD Attribute
- Modify the configuration of the existing Active Directory External Identity Source and select Edit
- Click “Attributes” tab
- Click “Add” > “Select Attributes from Directory”
- Enter the name of the test user previously modified to add the Static IP address and select “Retrieve Attributes”
- Ensure you tick the box “msRADIUSFramedIPAddress” and click “Ok”
American pie reunion hd free download. IMPORTANT – If you do not previously assign as static IP address to the user account you are using to query AD for the list of attributes the “msRADIUSFramedIPAddress” will not be in the list to select.
- Edit the attribute “msRADIUSFramedIPAddress” and change the “Type” value from STRING to IPv4
Anyconnect Static Ip Server
Create Authorization Profile
- Create a new “Authorization Profile” called “Static-VPN-IP-Address” – Policy > Policy Elements > Results > Authorization > Authorization Profiles
- In the Advanced Attributes Settings add a new value for “Radius:Framed-IP-Address” and equals the “msRADIUSFramedIPAddress” value previously added
NOTE – “LAB_AD” will equal the name of YOUR Active Directory
Modify Policy Set

- Modify the existing Policy and the “Static-VPN-IP-Address” Authorization Profile
Test AnyConnect VPN Client
- Log in to the VPN using the test client, once successfully authenticated you can check to see if the client has been assigned the correct IP address
- Within the RADIUS authentication logs double check to confirm the Framed-IP-Address value was used
How To Configure AnyConnect SSL VPN On Cisco ASA 5500
Repeating the test for a user that does NOT have a static IP address assigned with in AD continues to work and an IP address is assigned from configured IP Address Pool on the ASA.



