- Home; New features. The release notes site describes the new features introduced in XG Firewall 18.0. NAT Enhancements. XG Firewall’s NAT configuration receives a major update as NAT rules are now decoupled from Firewall Rules enabling more powerful and flexible configuration options including Source (SNAT) and Destination (DNAT) in a single rule.
- The article instructs you to configure the SSL / TLS Inspection feature on Sophos XG v18 devices, with the SSL / TLS Inspection feature that helps your system monitor the enterprise’s network operations with the Web and the application encrypted on the Internet.
We have made some changes to simplify our hardware support policy for SFOS. With this new policy, all current and previous XG and SG Series hardware models that can run v18 today will also be able to upgrade to future v18.x versions. This makes it easier for your customers to. Sophos Home offers clear and easy to understand subscription pricing. We offer one- and two-year pricing options, and discounts for continuing customers. Renewals are done automatically at the end of the subscription period, with clear communication via email about upcoming renewal events.
Table of lists
- Overview
- Diagram
- Deployment situation
- How to configure
- Testing with 2 PC
- Result
Overview
By Chris McCormack XG Firewall v18 Maintenance Release 4 (MR4) is packed with enhancements to performance, security, reliability, and the management experience. XG Firewall MR4 also enables great new Sophos Central Management capabilities. New Sophos Central enhancements.
The article instructs you to configure the SSL / TLS Inspection feature on Sophos XG v18 devices, with the SSL / TLS Inspection feature that helps your system monitor the enterprise’s network operations with the Web and the application encrypted on the Internet. That helps detect threats, viruses, and ransomware through encrypted protocols that other firewall devices cannot detect.
Diagram
Deployment situation
Enable the SSL / TLS Inspection rule and configure the HTTP scan policy and decrypt HTTPS on the Sophos XG firewall device
With PC1 we will add Sophos certificate, to check if PC1 has added Sophos certificate, the network traffic of PC1 is decrypted.
On PC2 we will not add Sophos certificate, to check that PC2 will drop traffic that Sophos cannot decrypt.

Mobile will not add Sophos certificate, to check the mobile device will drop traffic that Sophos cannot decrypt.
How to configure
- Log in to Sophos XG by Admin account
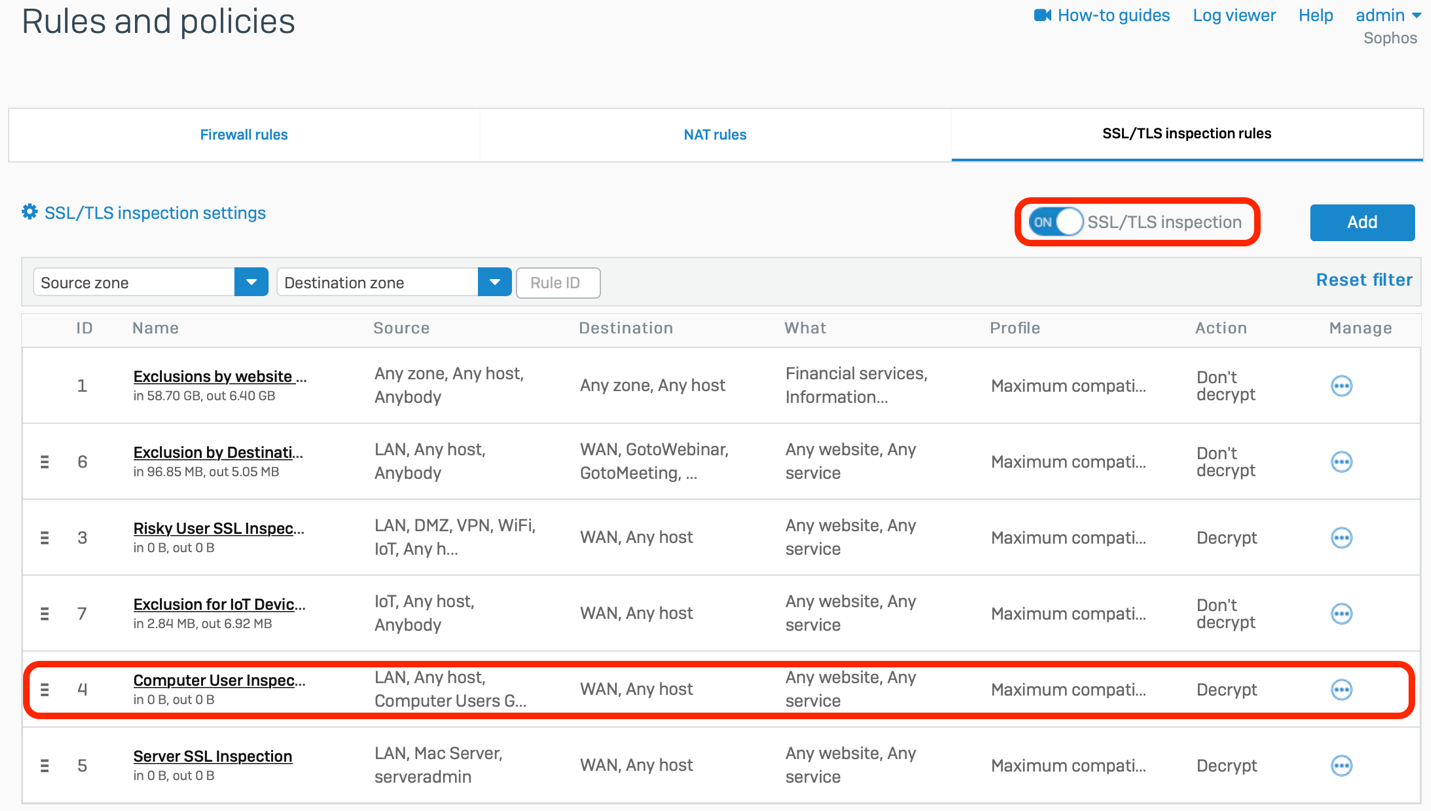
- Go to PROTECT -> Choose Rules and policies -> Go to SSL/TLS inspection rules -> Enable SSL/TLS inspection and click Add to create 1 SSL/TLS Inspection rule
- Enter name for SSL/TLS Inspection Rule
- In Action: Choose Decrypt
- Tick in Log connections
- In Decryption profile -> Click Create new
- Enter name for Decryption profile
- In Re-signing certificate authority -> Choose Use CAs defined in SSL/TLS settings
- In Non-decryptable traffic: Choose Drop in all items to prevent undecrypted traffic form going in the system
- In Block action -> Choose Reject & notify
-> Click Save
- In Source zones: Choose LAN
- In Source networkd and devices: Choose Any
- In Users and groups: Choose Anybody
- In Destination zones: Choose WAN
- In Destination networks: Choose Any
- In Services: Choose Any
- In Categorites and websites: Choose Any
-> Click Save
- Go to Firewall rules -> Choose LAN to WAN policy -> In Web filtering, choose Scan HTTP and devcrypted HTTPS
Sophos 18.0.3 Mr-3
Testing with 2 PC
After create policy SSL/TLS Inspecti
Both 2 PC cannot access Web
Add Sophos certificate on PC1
- Go to Certificates -> Choose Certificate authorities ->Click Download icon on SecurityAppliance_SSL_CA
- On PC1 add the downloaded certificate -> On the search bar, type mmc -> Click File -> Select Add/Remove Snap-in…
- Choose Certificate -> Click Add -> Choose Computer account if the computer uses Workgroup or My user account if the computer uses Domain
- Choose Local computer -> Click Finish
- In Certificates -> Go to Trusted Root Certificates -> Choose Certificates -> Right click choose All Tasks -> Click Import -> Search to where to save the downloaded Sophos Certificate

- After add certificate
Result
After add certificate for PC1
PC1 has accessed the web normally
PC2 still cannot access the web
Check log
PC1
PC2
Overview
Article configuring Nat Port for Panasonic switchboard equipment, so that outside the Internet can phone to the internal system
Here I use Panasonic VoIP switchboard
Port Switchboard is 5060 but because port 5060 is a spam port, the switchboard will change port public to the outside is port 31303
Port Voice of the switchboard is the port range 16000 to 16500

Diagram
How to configure

- Login to Sophos XG by Admin account
- Go to SYSTEM -> Choose Hosts and services -> In IP Host -> Click Add New -> Create host SwitchboardDevice1 with IP (192.168.4.10)
- Create a host similar to SwitchboardDevice2 with the IP (192.168.4.11)
- Go to Services -> Click Add -> Create Service with UDP protocol with 31303
- Create service with UDP protocol with 16000 to 16511
- Go to Rules and policies -> Choose NAT rules -> Click Add NAT rule -> Choose New NAT rule
- Create NAT rule with 31303 port to IP of SwitchboardDevice1 (192.168.4.10)
- In Original source: Choose Any
- In Original destination: Choose Any
- In Original service: Choose Service which was created before (31303)
- In Translated source (SNAT): Choose Original
- In Translated destination (DNAT): Choose 192.168.4.10
- In Translated service (PAT): Choose Original
- In Inbound interface: Choose Any or Port WAN
- In Outbound interface: Choose Any or Switchboard port
-> Click Save
- Create NAT rule with 16000 to 16511 port to IP of SwitchboardDevice2 (192.168.4.11)
- In Original source: Choose Any
- In Original destination: Choose Any
- In Original service: Choose Service which was created before (16000:16511)
- In Translated source (SNAT): Choose Original
- In Translated destination (DNAT): Choose 192.168.4.11
- In Translated service (PAT): Choose Original
- In Inbound interface: Choose Any or Port WAN
- In Outbound interface: Choose Any or Switchboard port
-> Click Save
- Go to Firewall rules -> Click Add firewall rule -> Choose New firewall rule
- Enter name: Allow WAN to TongDai
- In Source zones: Choose WAN
- In Source networks and devices: Choose Any
- In Destination zones: Choose LAN
- In Destination networks: Choose 2 IP of switchboard (192.168.4.10 and 192.168.4.11)
- In Services: Choose 2 Service which was created before (31303 and 16500:16511)
Sophos 18.0.4
-> Click Save
Sophos 18
YOU MAY ALSO INTEREST
